Automation Engineers Don’t Fail — Business Cases Do
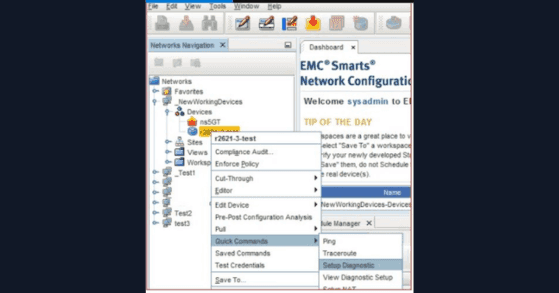
You have probably felt the frustration. You designed a brilliant automation solution, a script or workflow that could prevent critical outages, standardize hundreds of devices, and save thousands of hours of manual toil. Yet, the project is stuck. It sits in an approval queue, waiting for a signature that never seems to arrive. The common assumption is that leadership just doesn't "get it."